Possible Information Leak, Considered Unlikely

Possible Display Information Leak
On August 7th, Christian Reitter is announcing a possible side-channel data leak as a vulnerability across all hardware wallets which use OLED displays. At Coinkite, we’ve already mitigated it, even though we feel strongly that it is not a legitimate issue. In our opinion, it is both unproven (might not even work) and also completely impractical—even if it could be made to work perfectly.
TL;DR: Long-shot vulnerability breathlessly announced, install the latest firmware (v2.1.2) to get our just-in-case mitigations.
Background
We received an email earlier this year describing a possible issue and telling us to keep it secret for months. The idea was that the graphical display commonly used on hardware wallets, including the Coinkite Coldcard, was leaking information over the USB power lines about what it’s showing on the screen. Naturally enough, bright “ON” pixels take more energy than “OFF” pixels.
Your attacker would have to install monitoring hardware into the USB power source you use to power the Coldcard during the initial seed setup. We don’t know how bulky that would be, but if you use a trusted USB battery pack or AC adapter, you would be fine. If you’re like me, your home or office has hundreds of AC adapters and thousands of USB cables to choose from… Each of these would need the mythical “hardware implant” installed beforehand to get a chance to capture your seed the one time it is shown on screen.
We challenged Christian for more specific details and a proof of concept. He never really provided anything solid, just a few scope captures of varying noise and no solid evidence that it directly represented the screen contents. Normally, we’d expect to see a proof of concept demo, where he reconstructs the screen contents. That would make for a good presentation!
(Aside: We don’t appreciate how he’s doxed our company emails to others in the industry when he carelessly sends out bulk emails.)
The Risks
But what do we show on screen that’s a secret? Not much.
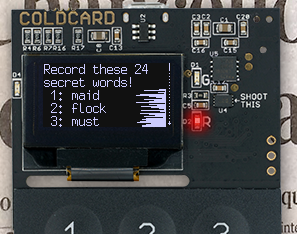
When you first setup a Coldcard, the seed words are shown on screen so you can write them down as a backup. That’s the only time this private key material is shown to the user.
Each digit of the PIN is shown briefly as you enter the PIN so that’s a hazard as well, but since there is no real-world implementation of this information leak, we don’t know if that’s long enough on screen to get a “good read” of the PIN digits.
The Solution
Coldcard firmware version 2.1.2, available for download already, has mitigations for both those areas: when entering the PIN, your digits are no longer echoed. Instead an X is shown, except if using a Mk1 device with it’s fine touch interface—you need the echo as a feedback.
For the few moments of the Coldcard’s lifecycle where the seed words are shown on screen, we’ve added masking noise along the right hand side of the screen. Since we don’t have a working proof-of-concept, it’s not possible to conclusively prove that this plugs the leak, but we feel the large amount of random noise on each line will be enough to swamp out any valid data that might be leaked on this side channel.
In future hardware, we intend to improve USB power supply filtering so that very little noise (or is it signal?) comes out of the Coldcard. That’s a broader mitigation and would help if some other, as yet unknown, information leak exists.
Credits
We’d like to thank Christian for being responsible in his disclosure of this issue, and it’s good we have researchers looking at these things. We hope that disclosure of unproven/minor issues doesn’t lead to fatigue or complacency in the community.
Christian applied for, and received CVE-2019-14356 as a code number
for the Coldcard version of this issue. We are not involved in
that process with MITRE.
Coldcard (Mark 2, second build) Available Now
Now with epoxy over the secure element!